
- Media library
- Question limits
- Creating a survey from MS Word doc
- How to edit live surveys
- Survey blocks
- Survey block randomizer
- Question randomization
- Scale Library
- What is monadic testing?
- What is sequential monadic testing?
- Extraction Support for Image Chooser Question Types
- What is comparison testing?
- Custom validation messages
- Survey Builder with QuestionPro AI
- Testing Send
- Survey Preview Options
- Add Questions From a Document
- Survey Authoring 2025
- Standard question types
- Multiple choice question type
- Text question- comment box
- Matrix multi-point scales question type
- Rank order question
- Smiley-rating question
- Image question type
- Date and time question type
- reCAPTCHA question type
- Net Promoter Score question type
- Van Westendorp's price sensitivity question
- Choice modelling questions
- Side-By-Side matrix question
- Homunculus question type
- Predictive answer options
- Presentation text questions
- Multiple choice: select one
- Multiple choice: select many
- Page timer
- Contact information question
- Matrix multi-select question
- Matrix spreadsheet question
- Closed card sorting question
- Flex Matrix
- Text Slider Question Type
- Graphical Rating Scales
- Rank Order - Drag and Drop
- Bipolar Matrix - Slider
- Bipolar Matrix Likert Scale
- Gabor Granger
- Verified Digital Signature
- Star Rating Question Type
- Push to social
- Attach Upload File Question
- Constant Sum Question
- Video Insights
- Platform connect
- Communities Recruitment
- TubePulse
- Open Card Sorting
- Map Question Type
- LiveCast
- Answer type
- Reorder questions
- Question tips
- Text box next to question
- Text question settings
- Adding other option
- Matrix question settings
- Image rating question settings
- Scale options for numeric slider question
- Constant sum question settings
- Setting default answer option
- Exclusive option for multiple choice questions
- Validate question
- Bulk validation settings
- Remove validation message
- Question separators
- Question Code
- Page breaks in survey
- Survey introduction with acceptance checkbox
- RegEx Validation
- Question Library
- Embed Media
- Slider Start Position
- Answer Display - Alternate Flip
- Matrix - Auto Focus Mode
- Text validations
- Numeric Input Settings- Spreadsheet
- Answer Groups
- Hidden Questions
- Decimal Separator Currency Format
- Allow Multiple Files - Attache/Upload Question Type
- Text box - Keyboard input type
- Deep Dive
- Answer Display Order
- Alternate colors
- Conjoint Best Practices
- Multi-media file limits
- Conjoint Prohibited Pairs
- Add logo to survey
- Custom Themes
- Display Settings
- Auto-advance
- Progress bar
- Automatic question numbering option
- Enabling social network toolbar
- Browser Title
- Print or export to PDF, DOC
- Survey Navigation Buttons
- Accessible Theme
- Back and Exit Navigation Buttons
- Focus Mode
- Survey Layout
- Survey Layout - Visual
- Telly Integration
- Telly Integration
- Workspace URL
- Classic Layout
- Branching - Skip Logic
- Compound Branching
- Compound or delayed branching
- Response Based Quota Control
- Dynamic text or comment boxes
- Extraction logic
- Show or hide question logic
- Dynamic show or hide
- Scoring logic
- Net promoter scoring model
- Piping text
- Survey chaining
- Looping logic
- Branching to terminate survey
- Logic operators
- Selected N of M logic
- JavaScript Logic Syntax Reference
- Block Flow
- Block Looping
- Scoring Engine: Syntax Reference
- Always Extract and Never Extract Logic
- Matrix Extraction
- Locked Extraction
- Dynamic Custom Variable Update
- Advanced Randomization
- Custom Scripting Examples
- Survey Logic Builder - AI
- Custom Scripting - Custom Logic Engine Question
- Survey settings
- Save & continue
- Anti Ballot Box Stuffing (ABBS) - disable multiple responses
- Deactivate survey
- Admin confirmation email
- Action alerts
- Survey timeout
- Finish options
- Spotlight report
- Print survey response
- Search and replace
- Survey Timer
- Allowing multiple respondents from the same device
- Text Input Size Settings
- Admin Confirmation Emails
- Survey Close Date
- Respondent Location Data
- Review Mode
- Review, Edit and Print Responses
- Geo coding
- Dynamic Progress Bar
- Response Quota
- Age Verification
- Tools - Survey Options
- Live survey URL
- Customize survey URL
- Create email invitation
- Personalizing emails
- Email invitation settings
- Email list filter
- Survey reminders
- Export batch
- Email status
- Spam index
- Send surveys via SMS
- Phone & paper
- Adding responses manually
- SMS Pricing
- Embedding Question In Email
- Deleting Email Lists
- Multilingual Survey Distribution
- SMTP
- Reply-To Email Address
- Domain Authentication
- Email Delivery Troubleshooting
- QR Code
- Email Delivery and Deliverability
- Survey Dashboard - Report
- Overall participant statistics
- Dropout analysis
- Pivot table
- Turf analysis
- Trend analysis
- Correlation analysis
- Survey comparison
- Gap analysis
- Mean calculation
- Weighted mean
- Cluster Analysis
- Dashboard filter
- Download Options - Dashboard
- HotSpot analysis
- Heatmap analysis
- Weighted Rank Order
- Cross-Tabulation Grouping Answer Options
- A/B Testing in QuestionPro Surveys
- Data Quality
- Data Quality Terminates
- Matrix Heatmap Chart
- Column proportions test
- Response Identifier
- TURF Reach Analysis
- Bulk Edit System Variables
- Weighting and balancing
- Conjoint analysis designs
- Conjoint part worths calculation
- Conjoint calculations and methodology
- Conjoint attribute importance
- Conjoint profiles
- Market segmentation simulator
- Conjoint brand premium and price elasticity
- What is MaxDiff scaling
- MaxDiff settings
- Anchored MaxDiff Analysis [BETA Release]
- MaxDiff FAQ
- MaxDiff- Interpreting Results
- Automatic email report
- Data quality - Patterned responses
- Data quality - gibberish words
- Import external data
- Download center
- Consolidate report
- Delete survey data
- Data quality - All checkboxes selected
- Exporting data to Word or Powerpoint
- Scheduled reports
- Datapad
- Notification Group
- Unselected Checkbox Representation
- Merge Data 2.0
- Plagiarism Detection
- IP based location data
- SPSS Export
- SPSS variable name
- Update user details
- Update time zone
- Teams
- Add Users
- Usage dashboard
- Single user license
- License restrictions
- Troubleshooting login issues
- Software support package
- Welcome Email
- User Roles & Permissions
- Bulk Add Users
- Two-Factor Authentication
- Network Access
- Changing ownership of the survey
- Unable to access Chat support
- Navigating QuestionPro Products
- Agency Partnership Referral Program
- Response Limits
Security
Introduction
This document outlines the updated security measures and protocols in place at QuestionPro. Our commitment to safeguarding data and ensuring the integrity of our systems is paramount. This document includes recent enhancements to our security infrastructure, including the integration of Cloudflare's Web Application Firewall (WAF), advanced network firewall strategies, and the utilization of VPNs for secure remote access.
Cloudflare's WAF is a cutting-edge, cloud-based solution that provides robust protection against a variety of cyber threats targeting web applications, APIs, and websites.
Advantages:- Enhanced Security: Offers robust defense against common vulnerabilities like SQL injection and XSS attacks.
- DDoS Protection: Effectively mitigates the risks of DDoS attacks.
- Performance Optimization: Improves website performance through global caching and optimization strategies.
- Seamless Integration: Easily integrates with existing infrastructures, eliminating the need for physical hardware.
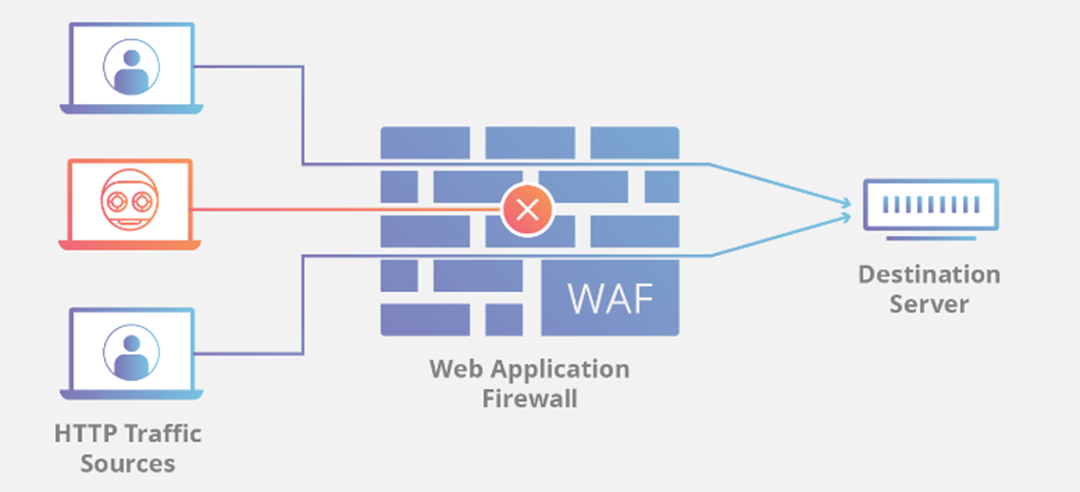
Overview:
Network centralized hardware firewalls serve as a primary defense mechanism against external threats, monitoring and controlling the flow of data in and out of the network based on pre-established security rules.
In the evolving digital landscape, securing systems against external threats is crucial. Traditional firewalls have been effective since the 1980s, but Next-Generation Firewalls (NGFWs) blend traditional and modern technologies for optimal digital protection.
- Monitors Network Traffic:
- Effectively analyzes incoming and outgoing data to prevent threats.
- Empowers IT teams to manage protection levels based on observed network activity.
- Stops Virus Attacks: Controls system entry points to thwart virus attacks. Mitigates potential immeasurable damage caused by rapidly evolving threats.
- Prevents Hacking: Crucial defense against unauthorized access to data, emails, and systems. Deters hackers or stops them entirely, safeguarding against data theft.
- Stops Spyware: Blocks spyware and malware infiltration into complex systems. Acts as a vital blockade against unauthorized access and data theft.
- Promotes Privacy: Proactively protects data, fostering trust with customers. Enhances competitiveness by showcasing robust data protection as a selling point.
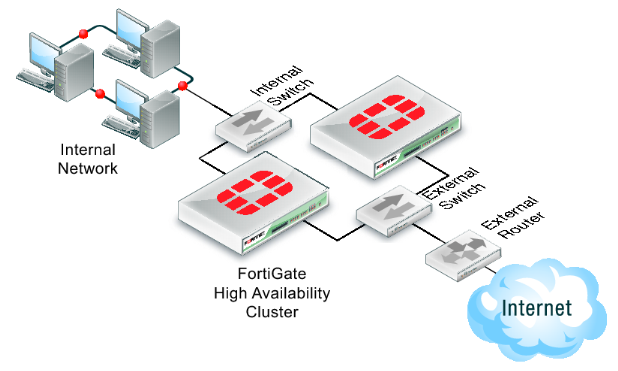
Network Firewall Advantages for Enhanced Security:
Our network security with Next-Generation Firewalls (NGFWs) with numerous benefits:
- Versatility: Real-time upgrades provide flexibility and adaptability. Centralized deployment facilitates quick adjustments to changing threat landscapes.
- Intelligent Port Control: Multi-layered protection surpasses traditional single-layer port approaches. Application-level security ensures better control, transparency, and data management.
- Simple Infrastructure: Streamlined infrastructure allows easy deployment of policies from one device. Transparent controls grant flexibility in managing network access.
- Updated Threat Protection: Integrated security measures (firewall, antivirus, ransomware protection, intrusion detection) enhance cooperation and simplify management. Deep packet inspection (DPI) provides a more informed decision-making process for data flow.
- Consistent Network Speed: NGFWs maintain high throughput without compromising security. Protect systems without sacrificing operational speed.
Description:
VPNs extend a private network across a public network, allowing secure data transmission as if the devices were directly connected to the private network.
Key features:- Secure Remote Access: Ensures secure access to corporate resources from any location.
- Data Encryption: Provides robust encryption for secure data communication.
- Privacy and Anonymity: Maintains user privacy and anonymity online.
- Geographical Freedom: Enables access to regionally restricted content and services.
Understanding the advantages and potential drawbacks of Virtual Private Networks (VPNs) is crucial for informed decision-making within your organization. Despite some limitations, the benefits of using a VPN can significantly enhance your business's security profile.
 Pros of VPN:
Pros of VPN:
- Secure Your Network: Effectively safeguards network integrity by preventing unauthorized access. Protects transmitted data, ensuring security and anonymity.
- Hide Your Private Information: High-level security, such as 256-bit encryption, conceals sensitive information. Mitigates the risk of hackers intercepting and misusing personal data.
- Prevent Data Throttling: Avoids service slowdowns imposed by internet service providers (ISPs) after data consumption. Conceals data usage, especially beneficial for mobile use and remote work.
- Avoid Bandwidth Throttling: Encrypts mobile traffic, preventing ISPs from intentionally slowing down internet speed. Enhances privacy by masking visited websites, reducing the likelihood of throttling.
- Get Access to Geo-blocked Services: Acquire a different IP address, enabling access to restricted content based on location. Facilitates unrestricted use of online services and information.
- Network Scalability: Cost-effective solution for expanding network access to multiple employees and remote workers. Enables running key applications in a secure cloud environment through the VPN tunnel.
- Reduce Support Costs: Shifts maintenance, performance checks, and security responsibilities to the VPN service provider. Offers potential cost savings by leveraging the service provider's infrastructure management expertise.
Site-to-Site VPN Overview:
A site-to-site Virtual Private Network (VPN) establishes a secure and encrypted connection between VPN gateways situated at different locations. This VPN tunnel encrypts data at its source, sends it over the public Internet, and decrypts it at the destination site before routing it to its final destination.
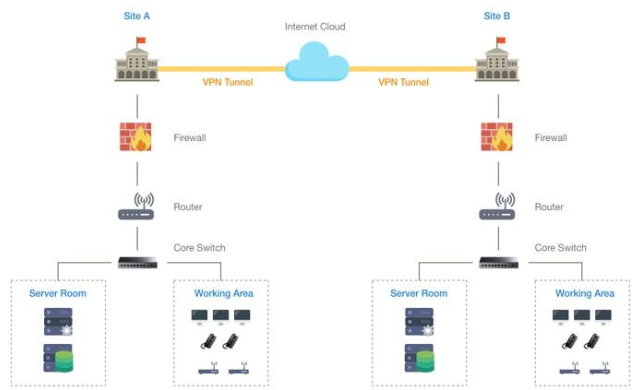
Benefits of Site-to-Site VPN:
- Secure Connectivity: Encrypts all traffic passing through the site-to-site VPN, ensuring the protection of business data against eavesdropping and unauthorized modification during transmission over the public Internet.
- Simplified Network Architecture: Facilitates the use of internal IP address ranges for devices within LANs. Eliminates the need to convert internal addresses to external ones for public Internet accessibility, maintaining the "internal" status of traffic between LANs.
- Access Control: Streamlines access control by treating site-to-site VPN users as "internal" users. Simplifies rule definition, allowing for easier management of network resources, particularly those restricted to internal access only. External users are inherently blocked from accessing these resources.
This feature is available with the following licenses :

